AVD(Android Virtual Device) for Mobile pentesting
AVD stands for “Android Virtual Device,” and it is an essential component of the Android software development environment. AVD is essentially an emulator that mimics the behavior of a physical Android device, allowing developers to test and debug their Android apps on a virtual device without the need for a physical phone or tablet.
While creating a testing device on Android Studio, I have faced some challenges which I would like to highlight in this blog post.
👉 Why my AVD (Android Virtual Device) is not giving me root access via adb?
Such scenarios may occur if you have selected an image with (Google APIs) or (Google Play) for your Android device.
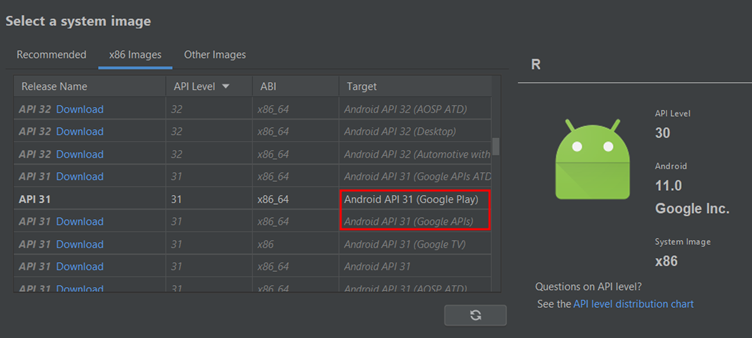
“Google Play APIs” images include Google Play services. Google Play services are a set of APIs and services provided by Google for Android apps. These services include features like Google Maps, location services, Google Sign-In, in-app billing, and many others.
“Google Play” images include both the Play Store app and the Play services.
So, in case you have selected images with “Google Play APIs” or “Google Play” then those images will not have root access.
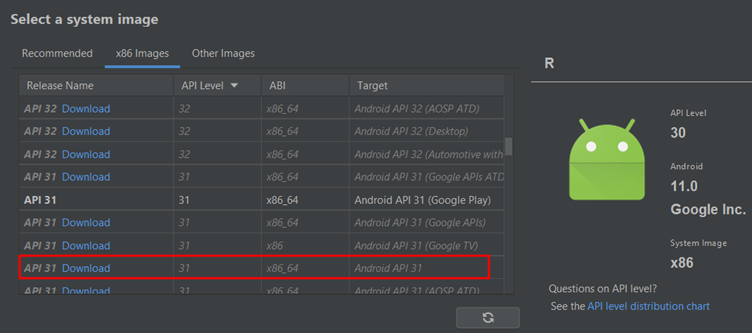
To have a root access to the device, select an image which do not have such services included keeping in mind your system architecture.
👉 I have a root access, but I cannot write to “/system” directory 😅
For the applications that targets API level 24 (Nougat 7.0) and above no longer trust user or admin added CAs for secure connections, by default.
In such cases we must add certificates in system CAs which require write permission on “/system” directory.
During the pentest, such scenarios may occur when the client application designed to run on the higher API levels. For example, Android Nougat and higher.
To add burp cert in system CAs refer to the awesome blog: Blog.
But before that we should have a writable access on the “/system” directory in the rooted device.
To do this start the device with the following flags.
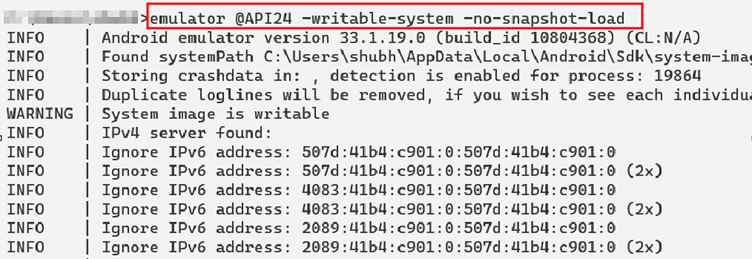
Now simply pass the commands:
adb root
adb remount
And you are ready to push certificate in the system directory. Please follow the blog to provide proper permission to the burp certificate.
✌ Note: Start the device with the same flags every time to have the files inside the system directory.
👉 I want PlayStore (Google Play) along with rooted access.
For this method we take a device with (Google Play) and then root it with rootAVD script.
Once we have the root access, we can then write a Magisk module to place burp certificate in the system directory wherever we want.
Here since the device has google services, I observed that "-writable-system" flag has no effect on the device.
And once the root access is taken with Magisk, the mounting operation for “/system” or “/” folders was giving the following errors.
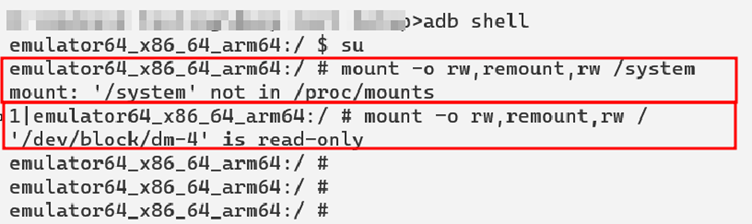
⏹ Following are the steps to root the device with Goole Play and burp certificate in “system” folder.
Choose a device with Play Store enabled
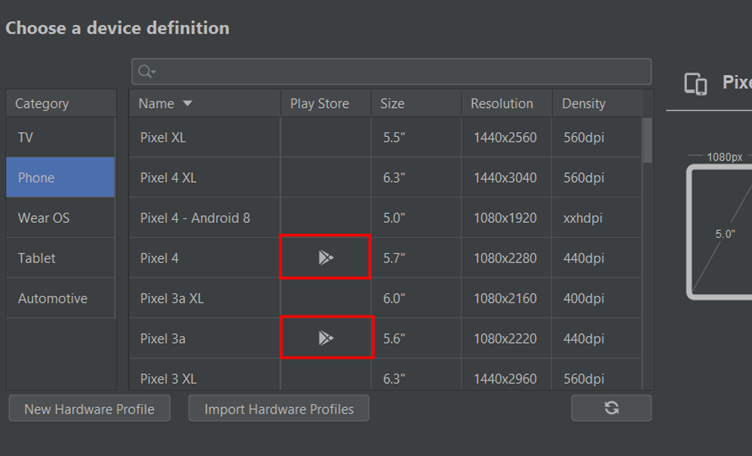
Now take an image with (Google Play)
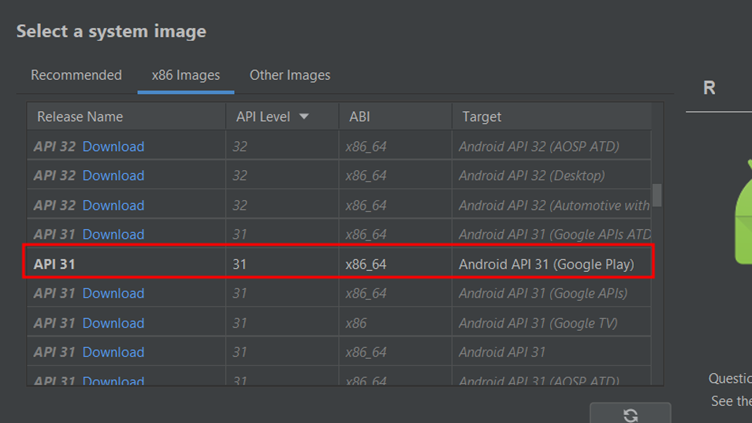
Now start the device and root it by following the steps on rootAVD
Once device is rooted, write a Magisk module to place burp cert in the “system/etc/security/cacerts”.
To write the Magisk module > Take root access of the device via
adband run the following commands:
## Create a Magisk module
mkdir -p /data/adb/modules/writable_system/system/etc/
## Copy the files and folders that should be writable to the Magisk module directory
cp -r /system/etc/security /data/adb/modules/writable_system/system/etc/security/
## Make the file in the Magisk module directory writable
chmod +w /data/adb/modules/writable_system/system/etc/security/
This will create a module in the Magisk named "writable_system"
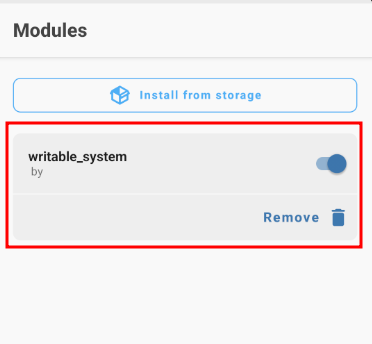
Magisk is able to write to the system storage because after the reboot all files in “/data/adb/modules/<modulename>” will be mapped to “/system” by Magisk
- Now place the burp certificate in the “/data/adb/modules/writable_system/system/etc/security/cacerts/” and reboot. Burp Certificate will be added to the system CAs 😃